What are various Message switching techniques?
AfterAcademy Tech
•
04 Feb 2020

Have you ever wondered what is the mechanism behind the video calls on Skype and WhatsApp? How our voice is sent over the earlier telephone calls? These facilities are provided to us by the various message switching techniques. Different massage techniques are used according to our requirements like the earlier telephone calls used circuit switching. In this blog, we will get the answers to all the above questions as we go through this blog. So, let's get started.
Message Switching Techniques
For transferring the message from the sender to the receiver we use various message switching techniques. The technique we use, depends upon the factors like kind of message we want to transfer, quality of the message, etc. In this blog, we will see all these techniques in detail.
There are three types of message switching techniques used:
- Circuit Switching
- Message Switching
- Packet Switching
Circuit Switching
Circuit Switching is a switching technique method that establishes a dedicated path between the sender and the receiver to send the data. The example of a circuit-switch network is a telephone network.
A communication through circuit switching has 3 phases:
- Circuit Establishment: In the first phase, a dedicated link is established between the sender and the receiver through a number of switching centers or nodes.
- Data Transmission: Once the connection is established data is transferred from the sender to the receiver over the connection established. This connection remains as long as the data transfer takes place.
- Circuit Disconnect: Once the data transfer is completed the circuit disconnects. The disconnection is initiated by one of the user i.e the sender or the receiver.
Example: Suppose we want to send the data from the A to B, we will first have to establish the connection in the switching nodes. These nodes establish a link such that there is a dedicate path from A to B. When the link is established the date is transferred. Once the data sharing takes place, the links are broken and are free to be used by some other systems.
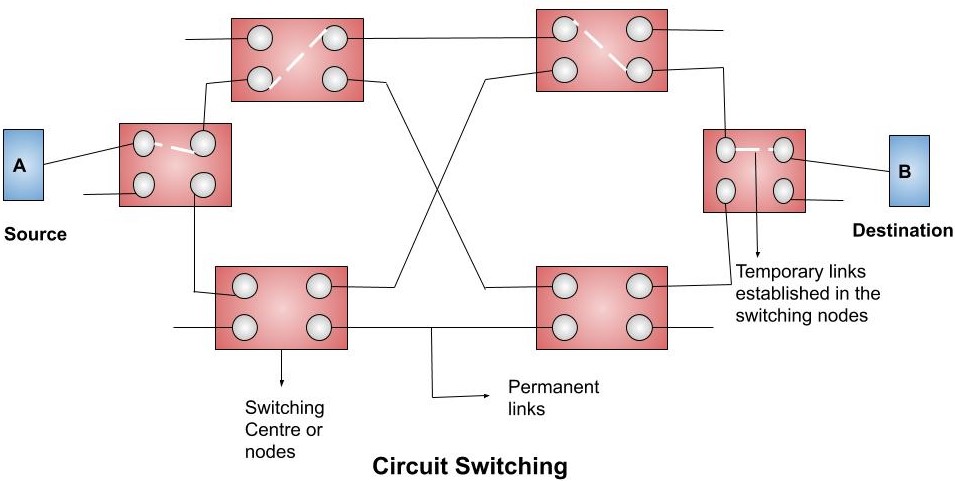
There are a number of paths available from a sender to a receiver. The sender can select any of the paths from the available paths.
Advantages of Circuit Switching Network
- Once the circuit is established there is no delay in data transfer. So it is useful in real-time data transfer like voice calls.
- The communication channel is dedicated which ensures a steady rate of data transfer.
- There is no need of packet sorting in the receiver's side because all the node follow the same path and in the same order.
Disadvantages of Circuit Switching Network
- As the channel is dedicated it cannot be used to transfer any other data even if the connected systems are not using the channel. Hence circuit switching is insufficient in terms of resource utilization.
- It is expensive as compared to other techniques because of dedicated path requirements.
- The time required to establish the connection between the source and destination is high. This means that there is no communication until the connection is established and the resources are available.
- It mainly used in voice traffic so not suitable for data transmission.
Message Switching
In-circuit switching when the source does not have enough data to transmit, the resources are unnecessarily kept idle. To avoid such situation Message switching is used. Message switching is a connectionless network in which the data from the source to destination is sent in the form of message units. A message is a logical unit of the information that can be of any length. The sender and the receiver are not directly connected. There are many intermediate nodes which ensure the delivery of the message to the destination. The message switching was used in sending telegrams.
It has two main characteristics:
- Store and Forward: The sender sends the messages to the nodes. The intermediate nodes store the complete message temporarily. The node inspects for any error and then transfers to the next node on the basis available free channel. Then the data of that node will be forwarded or transfered to the next node only if the next node has sufficient resources. The actual path taken by the message is dynamic as the path is established as it travels.
- Message Delivery: Each message must have a header that contains the routing information like source and destination address. All these pieces of information are wrapped in the message and then the message is sent from the source to destination.
Example: Suppose we have to send two messages i.e Message 1 and Message 2 from the sender to the receiver. We will directly send the message without establishing any connection.
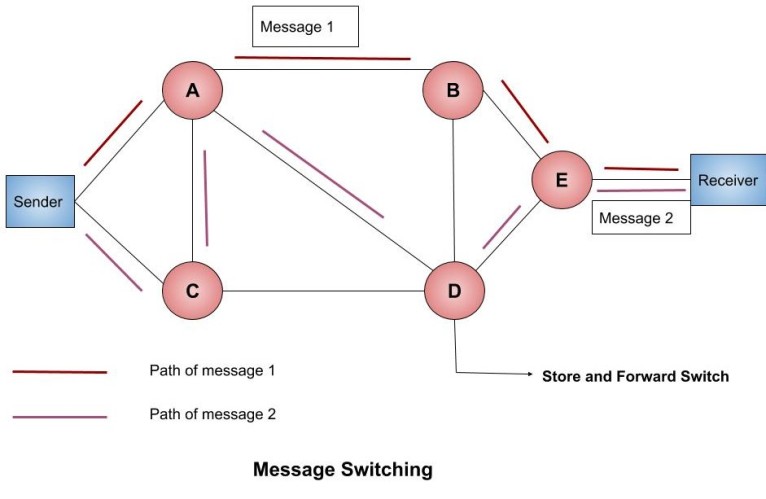
Advantage of Message Switching
- The efficiency is improved as a single channel can now be used for transferring many messages.
- The source and the destination don't need to be ready at the same time. Even if the receiver is not ready the sender can send the message and it can be stored by the nodes temporarily.
- The transfer of message is possible also when the transfer rate of the sender and receiver is different.
- It reduces congestion due to its store and forward property. Any node can be used to store the message until the next resources are available to transfer the data.
Disadvantages of Message Switching
- The store and forward method cause delay at each node. So, the primary disadvantage of message switching is that it cannot be used for real-time applications like voice or video calls.
- As the message can be of any length so each node must have sufficient buffer to store the message.
Packet Switching
Packet switching is a message switching technique in which the data is divided into packets. These packets contain a header that contains the information of the destination. The packets find the route with the help of this information.
The biggest packet-switched network is the internet.
A packet contains header and payload. The header contains the routing information and the payload contains the data to be transferred. The packet switching is also based on the Store and Forward method. Each packet contains the source and destination information so, they can independently travel in the network. The packet belonging to the same file may take different paths depending upon the availability of the path. At the destination, these packets are re-assembled. It the responsibility of the receiver to re-arrange the received packet to the original data.
Example: Suppose the data to be sent is divided into three packets i.e. 1, 2, 3. Now, these packets travel independently in the network. The intermediate nodes forward the nodes according to the availability of the channel. At the receiver side, the order of packets can be different. It is the duty of the receiver to re-arrange the received packets.
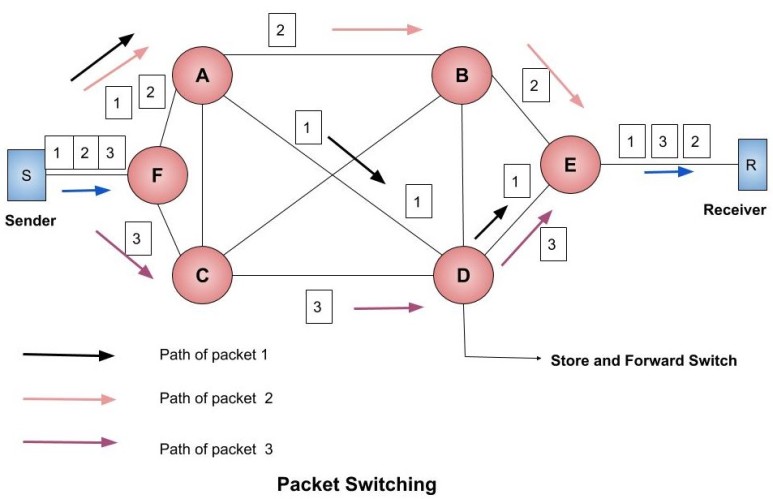
The path taken by the packet 1 is S → F → A → D → E →R. Similarly, the path taken by the packet 2 is S → F → A → B → E → R. Similarly, the path taken by the packet 3 is S → F → C → D → E → R.
Advantages of Packet Switching
- Packets have fixed sizes, so the switching devices do not require large secondary storage devices. The storage was a problem in message switching which is removed here.
- It is more efficient for data transmission as it doesn't require any dedicated paths.
- If the link is busy or not available, the packets can be re-routed. This ensures a reliable connection.
- The same channel can be used by many users simultaneously.
- With improved protocols, packet switching is used for applications like Skype, WhatsApp, etc.
Disadvantages of Packet Switching
- They cannot be used for applications that cannot afford delays like high-quality voice calls.
- Protocols used in packet-switching are complex and require higher implementation costs.
- If the network is overloaded then the packets may be lost or delayed. This may lead to loss of critical information.
- Sorting of received packets is required at the receiver's side.
Packet switching was originally designed to overcome the weakness of circuit switching. The circuit switching is inefficient for sending small messages. Also, the analogous(continuos) circuit makes it prone to noise and errors.
This is how various message switching techniques simplify the data transfer. Hope you learned something new today.
Do share this blog with your friends to spread the knowledge. Visit our YouTube channel for more content. You can read more blogs from here.
Keep Learning 🙂
Team AfterAcademy!
Written by AfterAcademy Tech
Share this article and spread the knowledge
Read Similar Articles
AfterAcademy Tech
What is Context Switching in Operating System?
In this blog, we will learn about the Context Switching in the Operating System. We will learn all the steps involved in Context Switching and in the end, we will see the advantages and disadvantages of Context Switching also.

AfterAcademy Tech
What is a Deadlock in DBMS and what are the deadlock avoidance, detection, and prevention techniques?
In this blog, we will learn what is a deadlock situation, what are various deadlock handling techniques like deadlock prevention, deadlock avoidance, deadlock detection, and deadlock ignorance.
AfterAcademy Tech
What are Routers, Hubs, Switches, Bridges?
In this blog, we'll learn about the networking devices such as Routers, Hubs, Switches, and Bridges. We'll also learn about the functionality, advantages, and disadvantages of these devices.

AfterAcademy Tech
What are the various types of constraints in SQL?
In this blog, we will learn various types of constraints that can be applied on a table. These constraints can be used to validate the data present in the table. We will learn about NOT NULL, UNIQUE, PRIMARY KEY, FOREIGN KEY, CHECK, and DEFAULT
