What are Proxy Servers and how do they protect computer networks?
AfterAcademy Tech
•
10 Feb 2020
The IP address which is given to your system by the ISP(Internet Service Providers) is used to uniquely identify your system. But there are many risks involved with the IP addresses like they might find personal information about you, spam you with “Personalized Ads”, etc. So, Proxy Servers or VPNs can be used to overcome this problem. In this blog, we will learn how the proxy server will protect your computer network. So, let's get started.
Proxy Server
The word proxy literally means a substitute. A proxy server substitutes the IP address of your computer with some substitute IP address. If you can't access a website from your computer or you want to access that website anonymously because you want your identity to be hidden or you don't trust that website then you can use a proxy. These proxy servers are dedicated computer systems or software running on a computer system that acts as an intermediary separating the end-users from the server. These proxy servers have special popularity among countries like China where the government has banned connection to some specific websites.
How does a proxy server work?
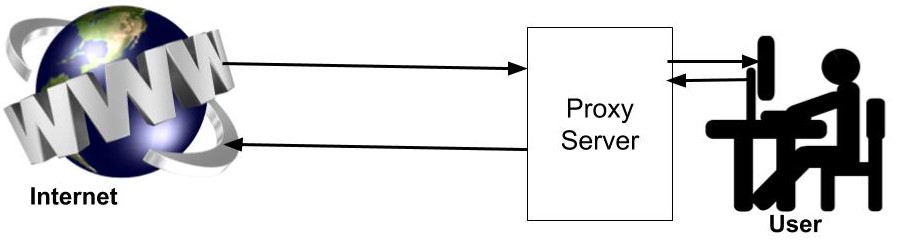
Every computer on the network has a unique IP address. This IP address is analogous to your street address which must be known by the post office in order to deliver your parcel to your home. A proxy server is a computer on the internet with its own IP address and the client which is going to use this proxy server knows this IP address. Whenever the client makes any request to any web server then its request first goes to this proxy server. This proxy server then makes a request to the destination server on behalf of the client. The proxy server actually changes the IP address of the client so that the actual IP address of the client is not revealed to the webserver. The proxy server then collects the response from the webserver and forwards the result to the client and the client can see the result in its web browser.
Types of Proxy servers
- Anonymous Proxy: An anonymous proxy is the most familiar type of proxy server and it hides the original IP address of the client and passes any anonymous IP address to the web server while making the request. By doing this, there is no way that the end-user receiving the request can find out the location from where the request was made. That's why most people use a proxy. This helps in preventing the identity thefts and keep your browsing habits private.
- High Anonymity Proxy: These types of servers change the IP address periodically This makes it very difficult for the webserver to keep a track of which IP address belongs to whom. TOR network is an example of a high anonymity proxy server. A high anonymity server has an advantage over the anonymous proxy in terms of privacy and security.
- Transparent Proxy Server: As the name suggests this proxy server will pass your IP address to the webserver. This is not used for the same purpose as the above two rather it is used for resource sharing. They are mainly used in public libraries and schools for content filtering. Example: If the students of a school are viewing the same article again and again via their school network, then it would be more efficient to cache the content and serve the next request from the cache. A transparent proxy can do this for the organizations.
- Reverse Proxy: Here the goal of the proxy server is not to protect you from while accessing the webpages but to stop the others on the internet form freely accessing your network. The most basic application of reverse proxy is that it protects the company resources and data on individual computers by stoping third party access on these computers.
Advantages of Using Proxy Servers
- Privacy: Individuals and organizations use the proxy server so that they can browse the internet more privately. The use of proxy protects them from identity theft and keeps their browsing habits safe. Many ISPs also collect the data of your browsing history and sell it to the retailers and government.
- Access to Blocked Resources: Several governments around the world restrict access to citizens to many websites and proxy servers provide access to the uncensored internet. Example: The Chinese government has blocked access to many websites for its citizens but a proxy server is all they need.
- Speed up Internet Surfing: Proxy Server also caches the data. So, if you ask for the website afteracademy.com then your request will first reach the proxy server. Proxy Server checks if it has cached this website. If it has cached it then you will get feedback from the proxy server which will be faster than directly accessing the website.
- To control Internet usage of Employee and Children: Organisations can use proxy servers and stop the employees from accessing certain websites (like Facebook )in-office hours. Parents can also use a proxy server to monitor how their children use the internet.
Risk of Using a Proxy Server
- The most common risk is spyware that gets downloads as free software. This is where the quality of your proxy server becomes more important. The proxy providers should have advanced security protocols so that the spyware is left passive and can't do any harm to our system even though installed. The proxy servers which don't have such kind of security allow the spyware to send your computer information and other personal data leaving the proxy servers useless.
- The proxy server has your IP address and web request saved mostly unencrypted. You must know if they save and log your data. You must know what are the policies that they follow. It is possible that they might sell your data to the vendors.
- This risk out of your control as the hackers can take control of the proxy server and monitor and change the data that comes over the proxy server.
This was all about why you need to use a proxy server and what are the risks associated with it. Hope you learned something new today.
Do share this blog with your friends to spread the knowledge. Visit our YouTube channel for more content. You can read more blogs from here.
Keep Learning 🙂
Team AfterAcademy!!
Written by AfterAcademy Tech
Share this article and spread the knowledge
Read Similar Articles
AfterAcademy Tech
What are Peer-to-Peer networks and Server-Based networks?
In this blog, we will learn about the types of network based on design, that are Peer-to-Peer, and Server-Based networks. We will also see the applications, advantages, and disadvantages of using these networks.

AfterAcademy Tech
What is a network and what are the nodes present in a network?
In this blog, we will mainly learn about a computer network and its node. We will also cover the classification, goals, and applications of a computer network.

AfterAcademy Tech
What is network topology and types of network topology?
In this blog, we will learn about various network topologies, their advantages and disadvantages in a computer network.

AfterAcademy Tech
What are the Data Transmission Modes in a network?
In this blog, we will learn about different data transmission modes based on the direction of exchange, synchronization between the transmitter and receiver, and the number of bits sent simultaneously in a computer network.