What is the OSI model and how it works?
AfterAcademy Tech
•
07 Feb 2020
Whenever you connect two devices either on the same or different networks, a question may arise in your mind regarding the connectivity of the devices. The two devices may have different architecture and implement different protocols, then how can they connect and share information with each other.
Actually, they need a standardized model that can be implemented by both to establish a connection between them. There are also some standardized protocols that they can implement to connect.
So, In this blog, we will learn about a widely accepted standardized model, i.e., the OSI(Open System Interconnection) model. We will also learn the mechanism, how two devices are connected using this model. We'll also focus on the different layers of this model along with their functionalities.
OSI Model
OSI model is a layered framework that allows communication between all types of the computer system. It has seven layers. OSI model is introduced by ISO(International Organization for Standardization) in 1984. Each layer has its own functionalities and calls upon the services of the layer just below it. These layers are a package of protocols that are implemented by computers to connect in the network. In other words, the OSI model defines and is used to understand how two computers connect with each other in a computer network.
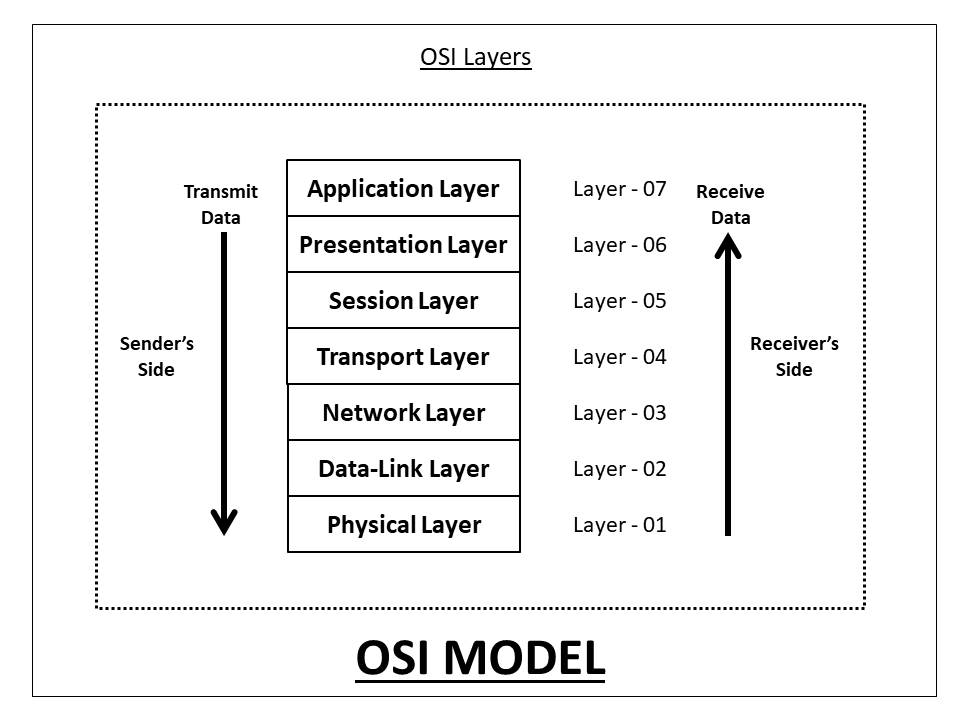
The seven layers of the OSI model, are as follows:
- Physical Layer
- Data-Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
We will learn about these layers and their functionalities one by one.
1. Physical Layer
The Physical Layer is the lowest layer of the OSI model and it deals with data in the form of bits or signals. The type of signal being generated depends upon the transmission medium. For example, if we are using copper wire or LAN cable, the output signal will be an electrical signal. Likewise, the output signal will be a light signal for optical fibre cable, and radio signal for air as a transmission medium.
At the sender's side, the physical layer will get the data from the upper layer and convert it into bitstreams(0's and 1's) and send it through a physical channel. At the receiver's side, it will convert the bitstreams into frames to be passed to the data-link layer.
Following are the functionalities of a physical layer:
- It defines the transmission media between two connecting devices.
- It also specifies the data rate(number of bits sent each second) over the defined media.
- It defines the topology of the network. The topology may be Bus, Ring, Star, Mesh, Tree, or Hybrid.
- It defines a data transmission mode. It can be Simplex, Half-Duplex, or Duplex.
- It defines the type of data encoding used in the transmission.
- It defines the line configuration of the network. It can be point-to-point or multiport.
2. Data-Link Layer
The Data-Link Layer is the second layer of the OSI model. It performs the physical addressing of data. Physical addressing is the process of adding the physical(MAC) address to the data. MAC(Media Access Control) Address is a 48-bit alpha-numeric number that is embedded in NIC(Network Interface Card) by the manufacturer. In other words, the data-link layer is embedded as software in the NIC which provides a means for data transfer from one computer to another via a local media. Thus, the data-link layer facilitates the transmission of data within the same network only.
The source and destination MAC addresses are included in the data header file by the data-link layer. At the sender's side, it receives the data in the form of packets from the network layer and converts it into smaller forms, called the data frame. At the receiver's side, it converts the data frame into packets for the network layer.
Following are the main functionalities of a data-link layer:
- Allows media access using framing: It allows the upper layers to access the media using framing, as it performs physical addressing of the data.
- Controls data: It performs flow, error, and access control of the data. It controls the data rate of the transmission to control the data flow. It uses the header information or checksum bits to control the error. Most importantly, it performs access control of the data using the MAC address.
3. Network Layer
The Network layer is the third layer of the OSI model. It mainly performs the transmission of data from one computer to another in different networks. This layer may not be so beneficial if we are transmitting the data in the same network. The network layer performs logical addressing(IP addressing) of the data. The source and destination IP addresses are included in the data header file by the network layer. The data is in the form of packets in this layer.
At the sender side, the network layer breaks the data segments received from the upper layer into smaller units, called data packets. Similarly, at the receiver's side, it reassembles the data packets into segments for the upper layer, i.e., the transport layer. Routers are mainly used in the network layer for routing purposes. Some of the protocols that are mostly used in this layer are OSPF(Open Shortest Path First), BGP(Border Gateway Protocol), IS-IS(Intermediate System to Intermediate System), etc.
Following are the main functionalities of a network layer:
- Logical Addressing: Every computer in a network has a unique IP(Internet Protocol) address. The network layer attaches the source and destination IP address to the data so that it can be transmitted even in different networks. Internet Protocol Version 4(IPv4) and Internet Protocol Version 6(IPv6) addressing are used by the network layer for logical addressing.
- Routing: Routing is a process through which the data packets can travel from one node to another in a computer network. In the network layer, the routing decisions are mainly based on IP addresses or logical addressing.
- Path Determination: Path determination is the process of selecting a path from various available paths based on the routing information. Path determination is done by the network layer for finding the most optimum path for data transmission.
4. Transport Layer
The Transport layer is the fourth layer of the OSI model. It is mainly responsible for the process-to-process delivery of the data. It performs flow and error control in the data for its proper transmission. The transport layer controls the reliability of communication through various functionalities.
At the sender's side, the transport layer receives the data from the upper layer and performs segmentation. The source and destination port numbers are also included in the header file of the data before forwarding it to the network layer. At the receiver's side, the transport layer performs the reassembly and sequencing of data. It reads the port number of the data from the header file, and then direct it towards the proper application.
Following are the main functionalities of a network layer:
- Segmentation: Dividing the data received into multiple data segments can be termed as segmentation. The transport layer performs the assembly as well as reassembly of data at the sender's and receiver's side respectively. Each segment has the source and destination 'port' and 'sequence' number. The port number helps to direct each data segment to the correct application, while the sequence number keeps them in a correct sequence when the segmented data is received at the receiver's side.
- Flow Control: The transport layer controls the flow of the data being transmitted. It is mainly done to avoid any data loss and enhance data transmission efficiency.
- Error Control: The transport layer checks for any kind of errors in the data using the checksum bits that are present in the data header. It can also request for retransmission of some data if it is not received at the receiver's end.
- Connection Control: The transport layer also maintains the connection between the devices in a proper way. For connection-oriented transmission, TCP(Transmission Control Protocol) is used. TCP is quite slow but is reliable in nature. It can be used for long-distance transmissions. For connection-less transmission, UDP(User Datagram Protocol) is used. UDP is fast but not reliable in nature. It is mainly preferred for short-distance transmissions.
5. Session Layer
The Session layer is the fifth layer of the OSI model. It mainly helps in setting up, closing and managing the connection in the network. Actually, whenever two devices get connected, a session is created, which is terminated as soon the connection is no longer required. The termination of the session is important to avoid the unnecessary wastage of resources. In other words, the session layer performs session management.
The session layer enables the devices to send and receive the data by establishing connections and also terminates the connection after the data transfer. It mainly performs authentication and authorization for establishing a secure connection in the network.
Following are the main functionalities of a session layer:
- Authentication: Authentication is a process of verifying the user. The session layer may ask the devices to enter valid login credentials, so as to maintain a secure data connection.
- Authorization: Authorization is the process of determining the user's authority to access the data. The session layer determines whether the device has permission to access those data elements or not.
- Synchronization: The session layer synchronizes the sender and receiver. It adds various checkpoints with the data to synchronize data at the sender's and receiver's side. In case of any crash or transfer failure, the data transmission can be resumed from the last checkpoint. There is no need to retransfer the whole data.
6. Presentation Layer
The Presentation layer is the sixth layer of the OSI model. It mainly performs data translation, encryption & decryption, and compression in the network. The presentation layer deals with the syntax and semantics of the information exchanged between two systems.
At the sender's side, it receives the data from the application layer and performs data encryption and compression to it. At the receiver's side, it receives the data from the transport layer and performs data translation, decryption, and uncompresses data.
Following are the main functionalities of a presentation layer:
- Data Translation: Data translation refers to transforming data from one form to the other. The presentation layer transforms the high-level user language data to the equivalent low-level machine-level language, and vice versa. Some of the standards used by this layer for translation are ASCII, EBCDIC, etc.
- Data Encryption and Decryption: Data encryption is the process of converting a plain text into cypher text for security. Encryption is applied to the data at the sender's side. Data decryption is the process of converting a ciphertext into plain text. It is applied to the data at the receiver's side. The presentation layer uses the SSL(Secure Socket Layer) for data encryption and decryption.
- Data Compression: Data compression is the process of reducing the number of bits in the data. It can either be lossy or lossless in nature. Lossless compression is mostly preferred for some important data items.
7. Application Layer
The Application layer is the topmost layer of the OSI model. This layer is mostly used by the network applications, that use the network. It mainly acts as an interface between the user and the network services. The Application layer provides services for network applications with the help of protocols. Some of the most widely used application layer protocols are HTTP, HTTPS, FTP, NFS, DHCP, FMTP, SNMP, SMTP, Telnet, etc.
Following are the main functionalities of an application layer:
- File Transfer: The Application layer mainly facilitates the file transfer between two network devices with the help of FTP(File Transfer Protocol).
- Web Surfing: Web surfing is possible only in the application layer. Some protocols like HTTP(Hypertext Transfer Protocol), HTTPs(Hypertext Transfer Protocol Secure), etc. enables web surfing.
- Emails: Electronic-mails can be sent from one device to another on the network only through the application layer. Some protocols like SMTP(Simple Mail Transfer Protocol), etc. are used for sending emails over the network.
- Network Virtual Terminal: The Application layer facilitates the remote host login in the network with the help of protocols like Telnet, etc. It can also be referred to as the software version of the physical terminal in the network.
This is all about the OSI model, its various layers and its functionalities. Hope you learned something new today. That's it for this blog.
Do share this blog with your friends to spread the knowledge. Visit our YouTube channel for more content. You can read more blogs from here.
Keep Learning 🙂
Team AfterAcademy!
Written by AfterAcademy Tech
Share this article and spread the knowledge
Read Similar Articles
AfterAcademy Tech
What is the TCP/IP model and how it works?
In this blog, we will mainly learn about the TCP/IP model and its working in detail. We'll focus on the features and working of each layer of the TCP/IP model.
AfterAcademy Tech
Which model is better, OSI or TCP/IP?
In this blog, we have described the similarities and dissimilarities between the OSI and TCP/IP models. We've also tried to tell which model is better for which scenario.
AfterAcademy Tech
What is an E-R model?
In this blog, we will see how an ER model is used in database designing. We will also see how an ER model is made using various components of the ER diagram. We will also discuss the features of an ER model along with its advantages and disadvantages.
AfterAcademy Tech
What is Data Model in DBMS and what are its types?
In this blog, we will learn about various data models present in DBMS. We will also learn about various types of data models present along with advantages and disadvantages of each model.